As the energy sector undergoes rapid digital transformation—from smart meters and microgrids to AI-driven wind farms and EV charging networks—it’s also becoming a new frontier for cyber threats. The CleanTech revolution brings connectivity, decentralization, and automation. But with those advances come novel vulnerabilities.
In 2025, cybersecurity isn’t just an IT issue for utilities and energy startups. It’s an existential risk. As systems grow smarter and more distributed, traditional security models are failing to keep up. The result? A widening threat surface that demands new strategies, new architectures, and new players.
Why CleanTech Is a Cyber Target Now
The convergence of digital and physical infrastructure has changed the stakes:
- Smart Devices Everywhere: Millions of new energy assets—rooftop solar inverters, battery systems, EV chargers—are now network-connected and often minimally secured.
- Rise of DERs and VPPs: Distributed energy resources and virtual power plants require real-time coordination across public and private networks. A breach in one node can ripple across the system.
- Legacy Systems Still in Play: Many utilities rely on outdated SCADA systems that were never designed for internet exposure. Attackers now exploit these as entry points.
- Nation-State Attention: Energy is a top-tier target for geopolitical cyber operations. The 2024 attacks on European hydrogen facilities and North American load balancers underscored this risk.

Where Today’s Defenses Fall Short
Traditional cybersecurity approaches—like perimeter firewalls and antivirus software—are insufficient for the CleanTech landscape. Why?
- No Clear Network Edge: With thousands of distributed endpoints and cloud-based analytics, there’s no single “front door” to defend.
- Data Flow Is Constant and Multidirectional: Modern systems are software-defined, continuously updating, and exchanging sensitive data across APIs and third-party tools.
- Security Isn’t Baked In: Many startups rush to MVP without security-by-design principles. Meanwhile, incumbent vendors struggle to retrofit protection into old devices.

Emerging Security Models and Solutions
Cybersecurity innovators and infrastructure stakeholders are beginning to adopt new models suited for the CleanTech era:
- Zero Trust Architecture (ZTA): Assume breach. Validate everything. Zero Trust replaces the idea of “trusted internal networks” with continuous authentication and least-privilege access.
- Software Bill of Materials (SBOMs): Developers and regulators now expect transparency into every component of a software stack. SBOMs make it easier to detect and remediate vulnerabilities.
- Cyber-Physical System (CPS) Security: Tailored solutions that protect not just data, but the physical systems it controls—like pumps, turbines, and transformers—are in high demand.
- Threat Modeling for Decentralized Energy: New frameworks are being built to simulate attacks on interconnected solar, storage, and EV networks and identify points of failure.
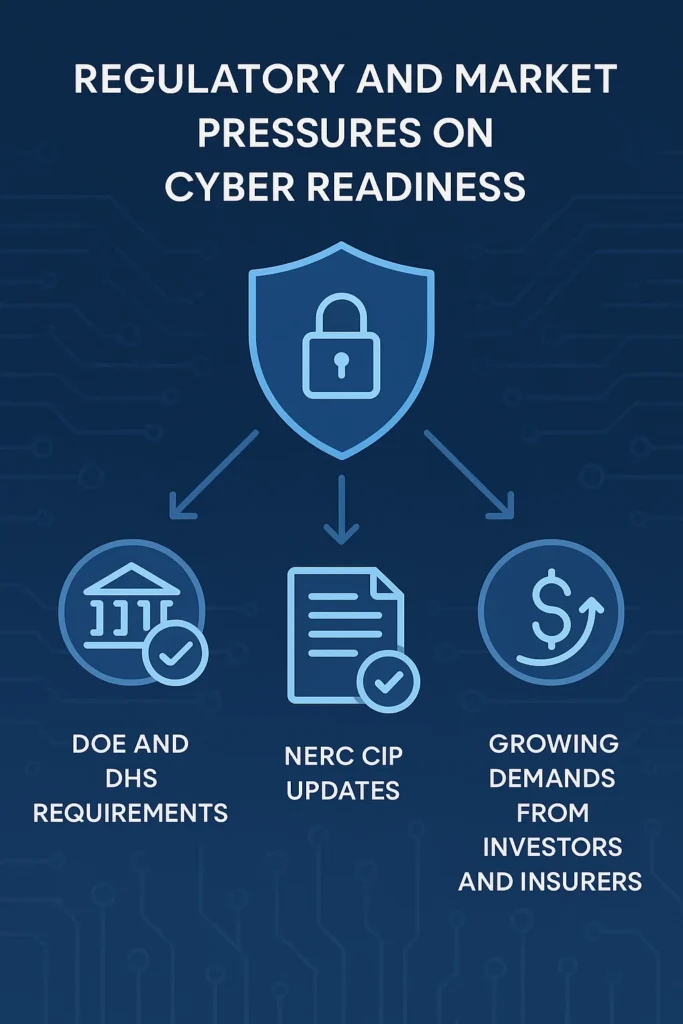
Regulatory and Market Forces Accelerating Cyber Readiness
The policy landscape is tightening:
- DOE and DHS Requirements: U.S. federal agencies are mandating stricter security standards for grid-connected devices and requiring cybersecurity plans for grant-funded projects.
- NERC CIP Updates: Bulk power operators face expanded compliance regimes focused on DER integration and third-party software risks.
- Investor and Insurer Demands: ESG investors and cyber insurance providers are now scrutinizing the security posture of CleanTech startups as part of risk evaluation.
How BridgePoint Labs Helps Build Secure CleanTech
At BridgePoint Labs, we work with early-stage startups, energy service providers, and infrastructure managers to:
- Build cybersecurity-by-design practices into CleanTech product development
- Conduct cyber risk assessments across decentralized energy architectures
- Prepare compliance documentation for DOE, NERC, and CISA standards
- Support proposal development for cybersecurity-focused funding programs, such as DOE CESER and DHS S&T
- Establish industry-academic partnerships for joint R&D in CPS security, data privacy, and threat intelligence
Use Case Highlights
- A smart grid startup integrated Zero Trust and anomaly detection protocols into its control platform, unlocking a $2.5M DOE grid modernization contract
- A university lab spun out a cybersecurity tool for EV charging networks and received Phase II SBIR funding with BridgePoint Labs’ proposal and compliance support
- A regional clean energy cooperative implemented continuous vulnerability monitoring with our help, strengthening its case for infrastructure insurance discounts
Key Takeaways
- Cybersecurity is now central—not optional—for CleanTech innovation
- Clean, distributed, and connected = vulnerable
- Investors and regulators are demanding cyber maturity early in the startup lifecycle
- Success depends on security by design, not afterthought
Cyber Resilience for the Climate Tech Future
BridgePoint Labs helps CleanTech companies, utilities, and infrastructure innovators integrate cybersecurity into every layer of their business—from architecture to compliance to funding.
In the race to decarbonize, don’t let security be your weakest link.